Breaking Out! of Applications Deployed via Terminal Services, Citrix, and Kiosks
In order to meet business requirements and client demand for remote access, many companies choose to deploy applications using Terminal Services, Citrix, and kiosk platforms. These platforms are commonly deployed in both internal networks as well as internet facing environments. In my experience, such application deployments are rarely locked down enough to prevent an attacker from breaking out to the underlying operating system. As a result, these systems can often be used as an entry point into the network and have the potential to provide attackers with unauthorized access to systems, applications, and sensitive data. The goal of this blog is to provide a simple process for testing common breakout scenarios using manual techniques and free tool kits. This should be useful to penetration testers and system administrators alike.
Below is an overview of the high level process and topics that will be covered:
- Obtain a common dialog box
- Bypass folder path restrictions
- Bypass file type restrictions
- Bypass file execution restrictions
- Bypass file black/white lists
- Obtain access to native interactive shells
- Obtain access to native management consoles
- Downloading third party applications
- Useful third party applications
Obtain a Common Dialog Box
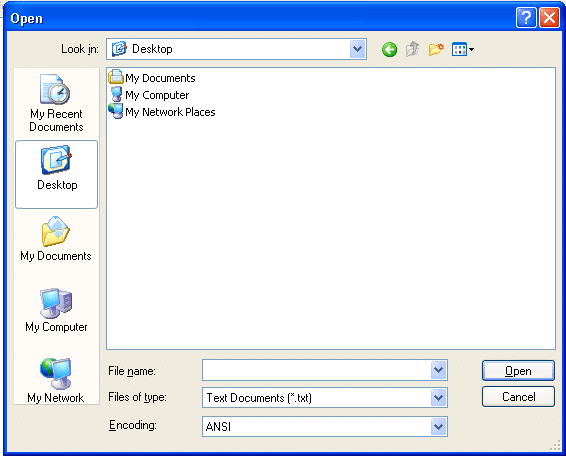
The first step towards breaking out of applications deployed via Terminal Services, Citrix, or a kiosk platform is often obtaining a Windows common dialog box. This is usually possible via keyboard shortcuts and application functionality that interacts with the file system. Windows XP dialog boxes look something like the screenshot below.
Windows Vista and above have additional built-in functionality for these dialogs such as Windows Search. However, a lot of those functions can be limited or removed via group policy settings. Regardless, there are a few ways that attackers and users are able to obtain a Windows dialog box.
Intended Application Functionality
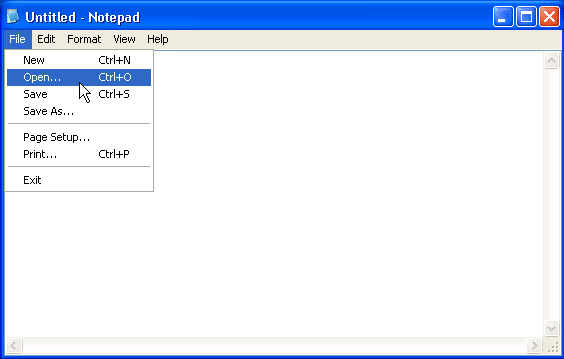
Many desktop applications deployed via Citrix and Terminal Services support functionality that allows them to interact with files on the operating system. Functions that allow users to save, save as, open, load, browse, import, export, help, search, scan, and print will usually be able to provide an attacker with a Windows dialog box. Below is a basic example using notepad.exe.
Shortcut Keys: Windows
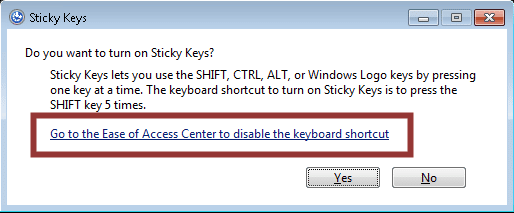
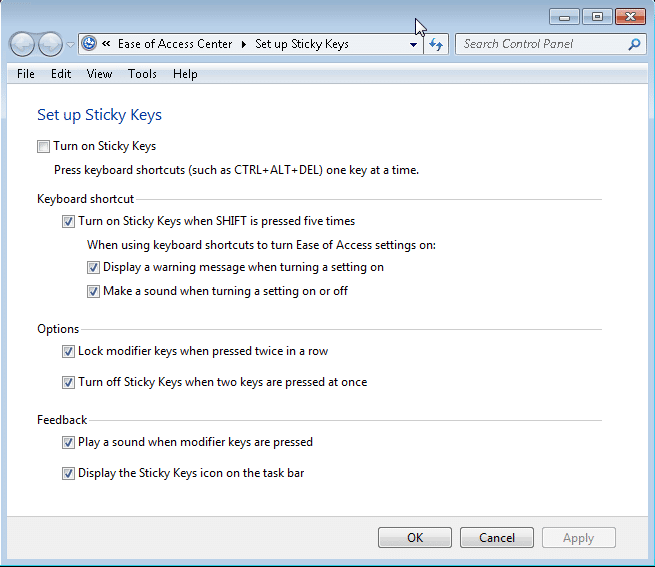
A lot of applications are deployed to environments that do not suppress default Windows shortcut keys via group policy or other means. As a result, attackers can often gain unauthorized access to other applications, menus, and dialog boxes. I have had a lot of luck with the accessibility option shortcut keys, but a larger list of default Windows shortcut keys can be found at https://support.microsoft.com/kb/126449. Also, the terminal services hardening guide (from Microsoft) can be found at https://technet.microsoft.com/en-us/library/cc264467.aspx. It provides some guidance for disabling most of the shortcut keys. Below is a basic example showing how to obtain an explorer dialog box using the “Sticky Keys” accessibility option shortcut keys.
1. Hit shift 5 times to obtain the Sticky Keys popup.
2. Click the link to access to open the explorer dialog box. In this instance, the explorer functionality can be accessed via the address bar.
Shortcut Keys: Citrix ICA Hotkeys
Citrix implementations have their own set of shortcuts or “hotkeys” that can lead to unauthorized system access. In some cases, custom hotkeys can be set in the ICA configuration file. Below are a few links that cover the default hotkeys, how to configure custom hotkeys, and how both can be disabled.
- https://support.citrix.com/article/CTX140219
- https://support.citrix.com/proddocs/topic/receivers-java-101/java-client-hotkeys.html
Internal Explorer Breakouts: Download and Run/Open
Most browsers support the execution of downloaded files from the browser. They also support running open files with their default program. So for example, a .txt file downloaded from a malicious web server would most likely open in notepad by default. Interactive Kiosk Attack Tool (iKAT) Desktop is a free Kiosk hacking framework that has some nice support for quite a few break out scenarios. However, in this instance the “File Handlers” and “iKat Tools” menus are particularly useful. It can be downloaded from https://ikat.ha.cked.net/Windows/index.html.
Internal Explorer Breakouts: Menus
A lot of web applications are deployed via Terminal Services, Citrix, and Kiosk platforms. Most of them are made accessible via Internet explorer. As it turns out Internet Explorer is very integrated with the Windows operating system. As a result, it can be used to navigate to folders, execute programs, and download content via native functionality. Common areas that can be used to break out of Internet Explorer include, but are not limited to:
- The address bar
- Search menus
- Help menus
- Print menus
- All other menus that provide dialog boxes
- Right-click menus that support things like:
- Goto/search copied address functionality
- View source functionality
- Third party plug-ins
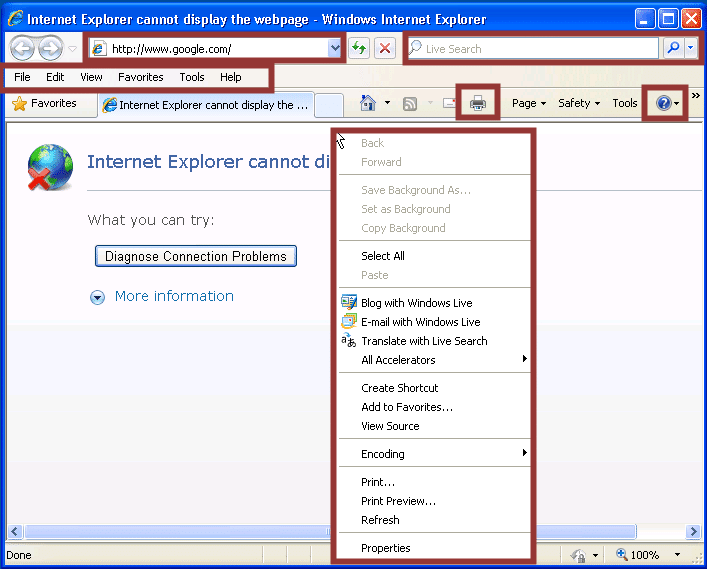
Below is a basic screen shot of Internet Explorer. I’ve outlined a few of the common functions/menus that can be used to break out to other applications or obtain a dialog box.
Internal Explorer Breakouts: Menu Links
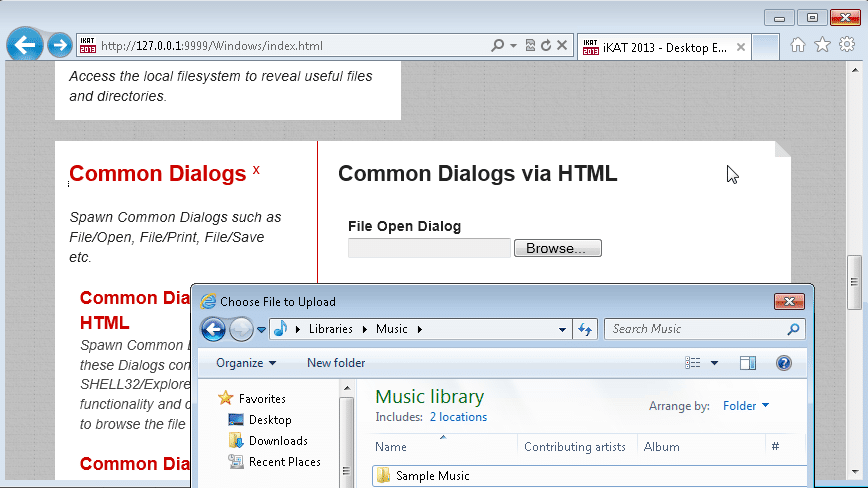
In Internet Explorer you can also access common dialog boxes via HTML hyperlinks. iKat Desktop has included a module to launch dialog boxes through such links. In order to leverage the module simply start iKat, navigate the iKat web server via the target application, and click on the links in the “Common Dialogs” menu. Below is a sample screen shot.
To be fair I’ve also provided a few links related to locking down Internet Explorer and placing it into “kiosk mode” to help prevent attackers from using it to breakout to the local operating system.
- https://technet.microsoft.com/en-us/library/cc775996%28v=ws.10%29.aspx
- https://social.technet.microsoft.com/Forums/en-US/winserverGP/thread/207ef293-2a5c-461a-aafb-630caacd3d56/
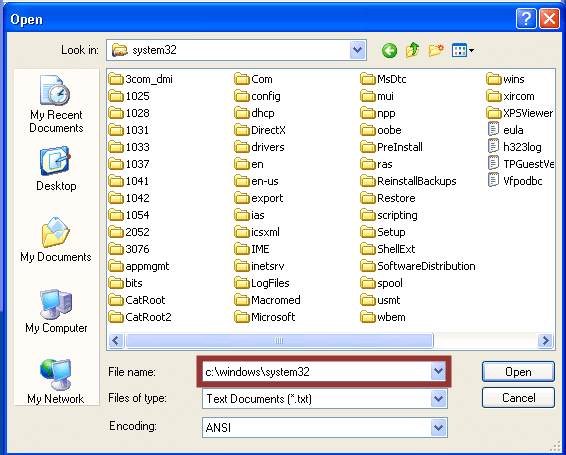
Bypass Folder Path Restrictions
After obtaining a Windows dialog box, the next step is often to navigate to a folder path that houses native executables that can provide an interactive console, registry access, etc. Usually you can simply type the folder path into the file name field, but sometimes you will have to use alternative options. Below are some options that typically work in both explorer and Internet Explorer. Most of them can be prevented via group policy or registry modifications.
Standard Folder Paths
A standard file path looks like “C:WindowsSystem32” and can be entered into the file name field in order to navigate to the desired folder. Below is a basic screen shot example from Windows XP.
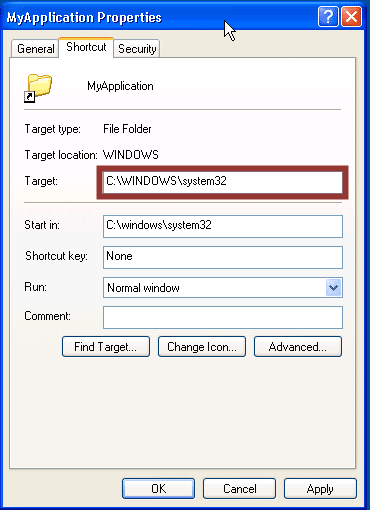
Folder Paths in Shortcut Links
In a handful of instances I’ve found it useful to modify existing Windows shortcuts to gain unauthorized access to folder paths. Below are the basic steps.
- Right-click the shortcut
- Choose properties
- In the “Target” field change the path to the folder you wish to access.
Below is a sample screen shot of what the shortcut properties window should look like for an application named “MyApplication”.
Folder Path Alternatives: Environmental variables
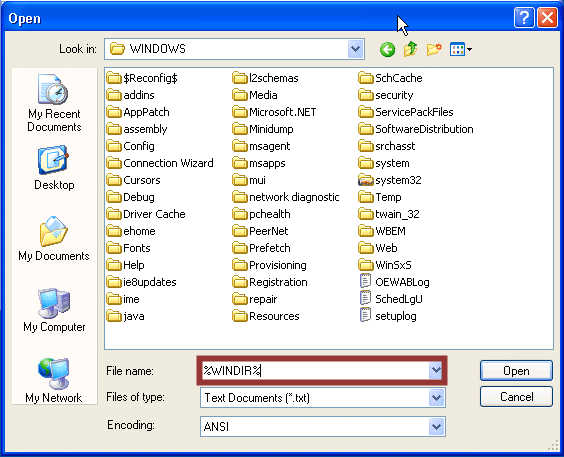
By default, Windows sets a number of environmental variables that can be used almost anywhere in Windows (including file dialog boxes). To view the standard environmental variables you can type “set” in a command console. In most cases you should be able to type the variable into the Filename and gain some access to the relative directory. Below are some default variables to get you started.
- %USERPROFILE%
- %PROGRAMDATA%
- %PUBLIC%
- %TMP%
- %WINDIR%
- %SYSTEMDRIVE%
- %SYSTEMROOT%
Below is a basic screen shot example.
Folder Path Alternatives: Shell URI Handlers
There are a lot of folder locations that can be accessed via shell command shortcuts. Many of which will allow you to execute programs, and provide some level of write access, that will come in handy later on. I have not been able to find any solid Microsoft documentation on this, but there are quite a few sites online with good command lists. One of which is https://docs.rainmeter.net/tips/launching-windows-special-folders. Below are a few shell command examples. They can be executed from the run menu, taskmgr, command console, or the file name/path fields in a Windows dialog box.
- shell:DocumentsLibrary
- shell:Librariesshell:UserProfiles
- shell:Personal
- shell:SearchHomeFolder
- shell:System shell:NetworkPlacesFolder
- shell:SendTo
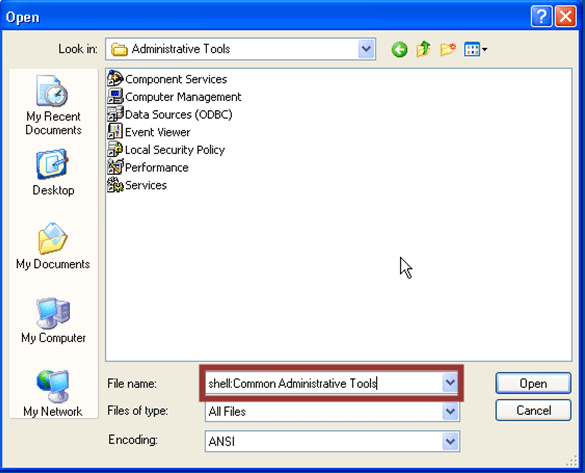
- shell:Common Administrative Tools
- shell:MyComputerFolder
- shell:InternetFolder
Below is a basic screen shot example showing how the “shell:Common Administrative Tools” command can be issued in the file name field to access a folder containing shortcuts to administrative tools.
It’s worth noting the common Shell handler commands can be found in the iKat Desktop “File System Links” menu.
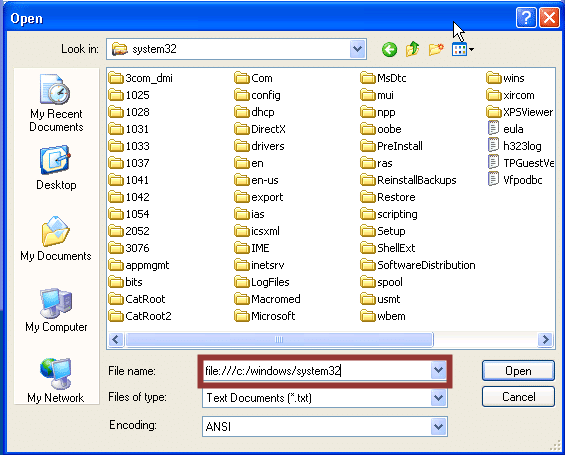
Folder Path Alternatives: File Protocol Handler
Below is an example of how to use the file handler to access a folder path. Enter the path into the filename and press enter to change the directory. A file handler folder path looks like “file:///c:/Windows/System32/”.
There are a number of other native protocol handlers that can be targeted as well. iKat has a menu that contains a list of the common ones, but I’ve provided a short list of them below to give you an idea of the potential.
- data:
- res:
- about:
- mailto:
- ftp:
- news:
- telnet:
- view-source:
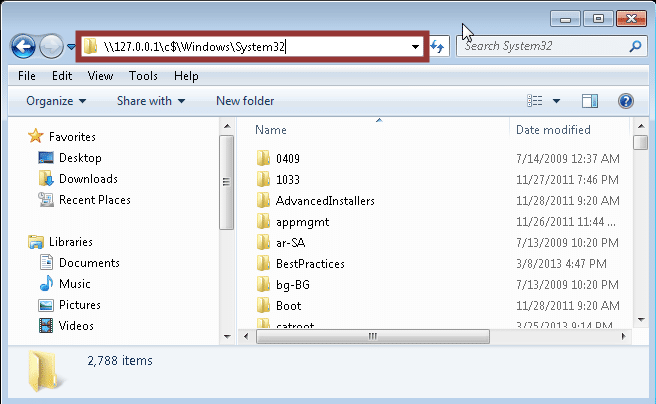
Folder Path Alternatives: UNC Path
In many cases UNC paths can be used to bypass group policy restrictions preventing you from accessing all of your favorite file paths. Below is a basic screen shot showing how a UNC path can be used to navigate to the “c:windowssystem32” directory of a Windows 7 system via the address field. It should be noted that you can use the file protocol handler and UNC paths together.
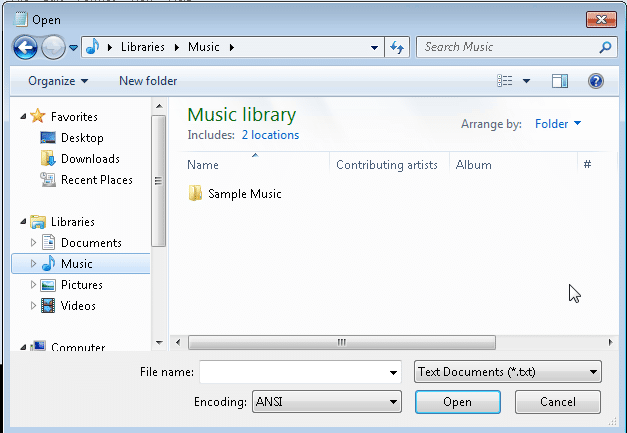
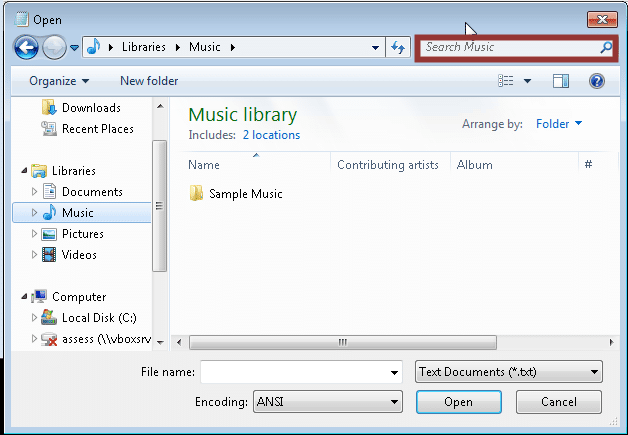
Windows Search
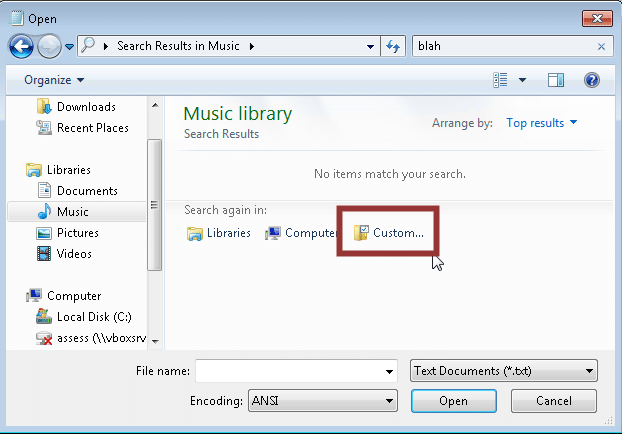
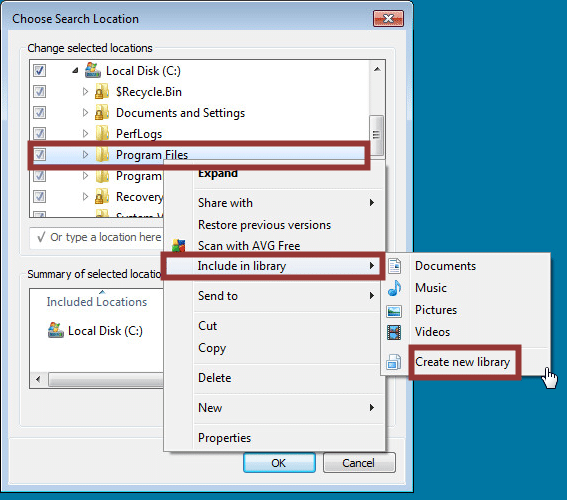
The native search functionality in Windows can often be used to navigate the operating system even with restrictive policies in place. For example, performing a search and then clicking the “custom” menu will at a minimum provide a full list of the folders on of the operating system even if the file restrictions have been put into place by GPO. In some cases you may even be able to break out to your personal directories. This can be accomplished using the steps below:
1. Obtain a dialog box
2. Search for any string
3. Click “Custom…”
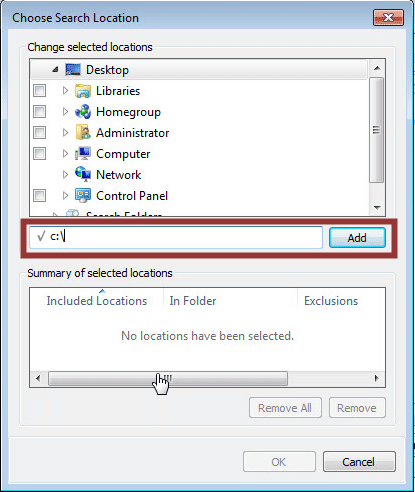
4. Add a custom search path for “c:”
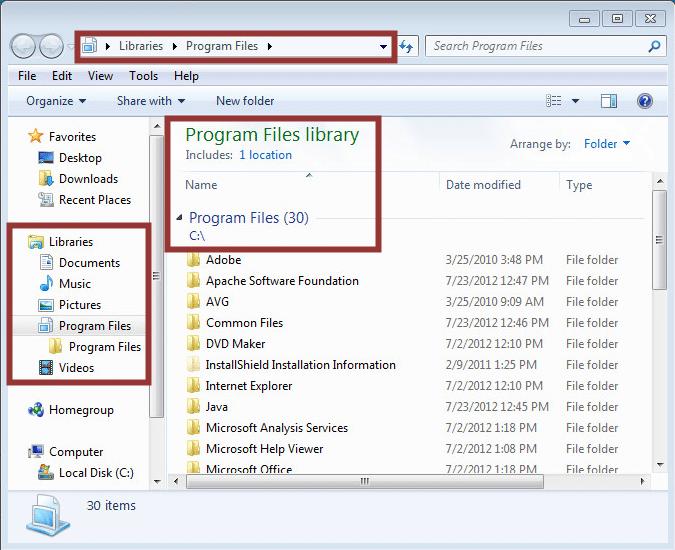
5. Expand the “c:” and right-click the sub directory that you would like to access. Then choose “Include in library->Create new library”.
6. A soft link to the location will be created in your personal libraries folder, and the folder will be automatically opened. In some case allow you to access folders and files that you shouldn’t have access to.
There are also some more advanced search commands that can help you refine searches for key files during your breakouts at the sites listed below.
- https://windowssecrets.com/top-story/getting-the-most-from-windows-search-part-2/
- https://windows.microsoft.com/en-us/windows7/advanced-tips-for-searching-in-windows
Bypass File Type Restrictions
Sometimes dialog boxes will be deployed so that only certain file types or folders can be viewed. Most of the time this can be bypassed by entering wild card characters into the filename field and pressing enter. I provided some basic examples below, but didn’t feel this one really warranted a screen shot.
- *.exe
- *
- *.*
Bypass File Read Restrictions
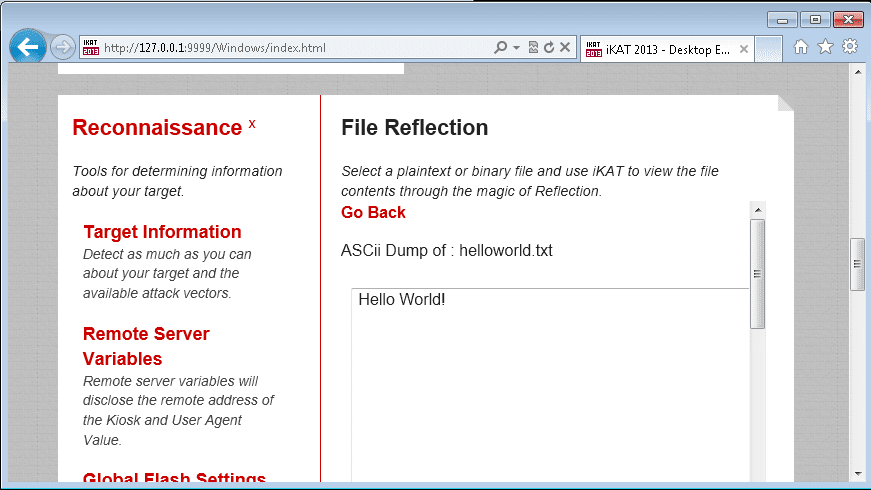
In some cases you may not have the ability to launch applications to read files on the operating system. However, in many cases you can upload files to an evil web server via an upload form via your web browser. iKat Desktop actually has a module called “File Reflection” in the “Reconnaissance” menu to a serve that purpose. Below is a screen shot example showing the upload and viewing of a file called “helloworld.txt” that contains the string “Hello World!”.
Bypass File Execution Restrictions
The fantastic thing about Windows is that there is always more than one way to do everything. Naturally this makes Windows easier for users, but it also makes it harder to lock down. Below are a few different options for executing files when standard execution isn’t possible.
Right-Click and Open
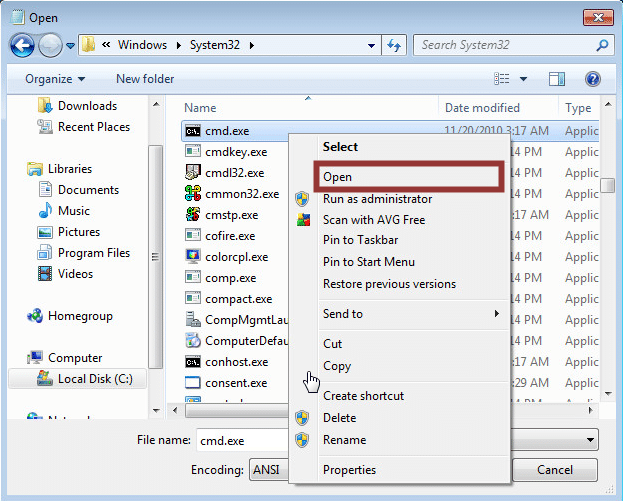
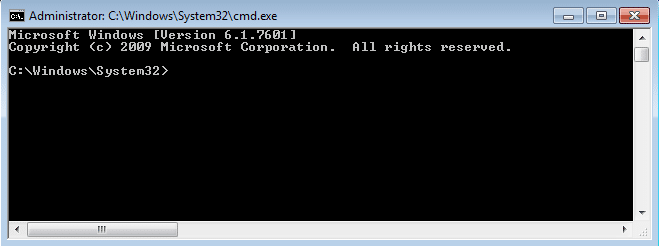
The classics never die. If accessing right-click menus is possible then simply right-click the file you wish to execute and choose open from the Windows file dialog box. Below is a basic example showing how to run cmd.exe
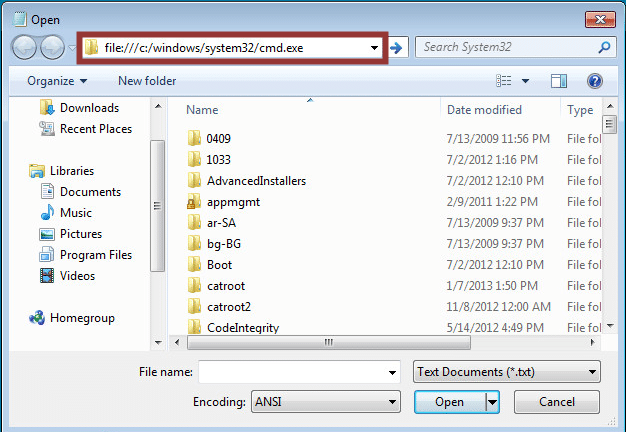
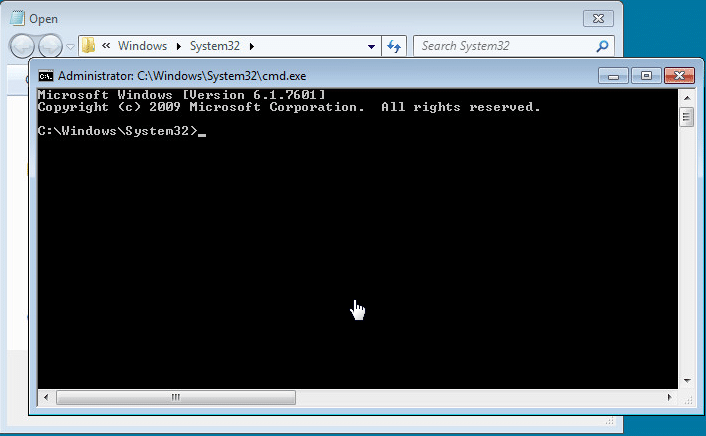
File Protocol Handler
In most scenarios this works well in the address bar for both Internet Explorer and Windows Explorer. To execute a file with this method type “file:///c:/Windows/System32/cmd.exe” into the address bar. Below are a few screen shots to illustrate the process. Once again, this can also be done using iKat by clicking on a preconfigured hyperlink.
File Shortcuts
Some “restricted” desktops and dialog boxes may allow you to modify or create shortcuts to the files for execution. After the shortcut is modified/created a simply double-click should do the trick.
- Right-click the shortcut
- Choose properties
- In the “Target” field change the path to the executable you wish to run.
Below is a basic example screen shot.
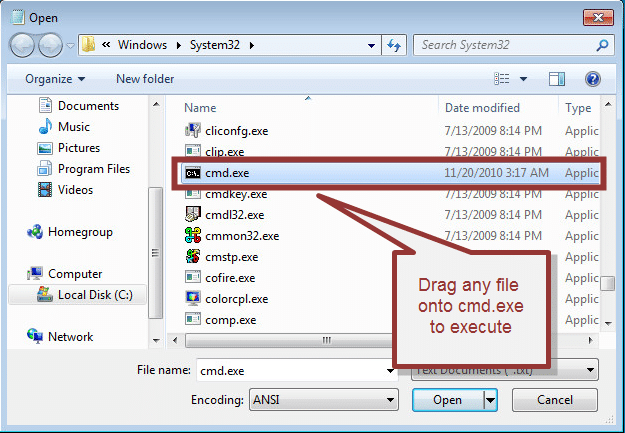
Drag and Drop Execution
Windows also allows for drag and drop execution. For example, if right-click or file handler options are unavailable, you can simply drag any file onto cmd.exe in order to open a console Window. This can be done with a single dialog or between multiple as shown in the basic example below.
Browser Add-ons
If you’re testing a web application in most cases you’ll have the ability to navigate to a web server via the address bar in Internet Explorer or Windows Explorer. By starting up your own web server on a remote server you should be able to access add-on applications that have the ability to pass commands to the operating system. For example, you can use a Java applet that passes commands through cmd.exe and displays the results on the page. Below are some common technologies that can be used. If you don’t feel like writing your own wrappers, iKat supports a number of different “Browser Addons” including java applets, click once, and ActiveX.
Browser Based Exploits
Many browsers and browser add-ons suffer from exploits that allow the execution of arbitrary code on the system. One way to leverage those kind of issues while trying to break out an application deployed via Terminal Service, Citrix, or Kiosk platform is to simply visit a web page hosting the exploit. You can configure and deploy your own malicious web pages with Metasploit manually or through iKat. However, Metasploit provides the flexibility to test one module at a time or test many at once with the “browser_autopwn” module. I would provide instructions, but the usage has been documented a million times. Feel free to Google it.
Office File Macros
Office and Adobe PDF documents can contain macros that will execute arbitrary code on the system. Simply create an Office file that with run the operating system command of your choice via a macro, host it on your malicious web server, and open it from the application’s browser or Internet Explorer. Surprise! iKat supports this as well.
Native Application Functionality
A surprising number of applications have command execution functionality built in on purpose. So make sure that you walk through the entire application looking for command execution, scheduled tasks, and database query options. Many thick applications also provide users with the ability to execute arbitrary queries on backend databases. In many cases that functionality can be used to execute operating system commands through existing database functions on the database server such as xp_cmdshell.
Bypass File Execution Black/White Lists
Administrators can configure group policy to prevent or allow applications to be run by name. However, attackers have a few workarounds available to them which can be hard to prevent with group policy on its own. Below are a few examples.
Rename files
Simply renaming files will typically allow you to bypass group policy enforced black and white lists. In most cases you can rename your files to anything that isn’t on the blacklist, but I have had the most success when naming files after required or running processes like svchost.exe, conhost, explorer.exe, iexplore.exe, etc.
Change Directories
Although the default folders used by the application may not allow files to execute, your user’s personal directories usually do. Navigating to %userprofile% or shell:Personal will often give you the write/execute access you’ll need to break out of the application and execute commands on the operating system.
Obtain Access to Native Interactive Shells
There are lots of native applications that will provide an interactive shell. I’ve listed a few of the common ones are below:
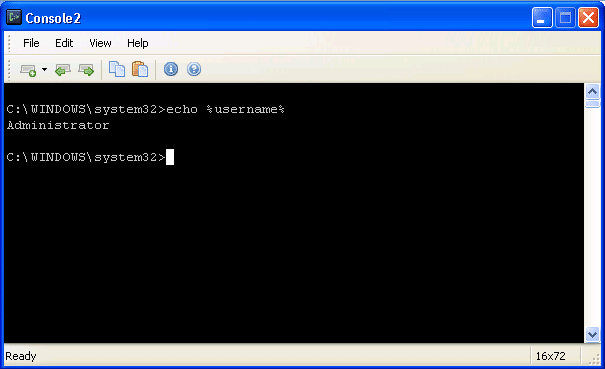
CMD.exe
Cmd.exe is the native console for Windows. I think most people are more comfortable with it than the alternatives just because it’s familiar. However, use what you like. Below is a basic screen shot example.
It’s worth noting that there are two version of cmd.exe in 64bit Windows systems. The are located in c:windowssystem32 and C:WindowsSYSWOW64cmd.exe.
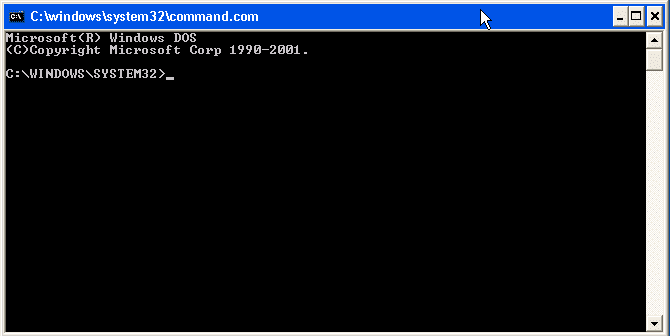
COMMAND.com
Everyone goes straight for cmd.exe, but don’t forget about command.com. It’s still on older Windows systems and when everything else is locked down it can come in handy. Below is a basic example screen shot.
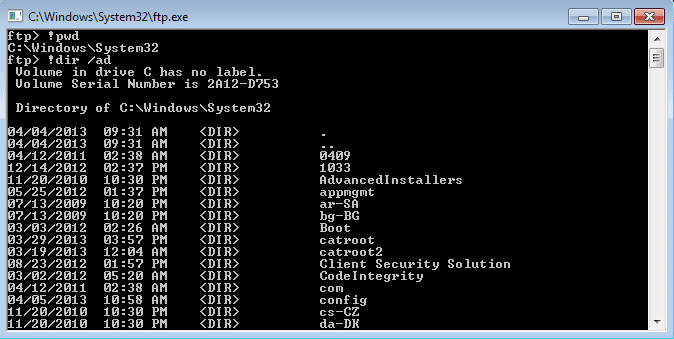
FTP.exe
A lot of people forget that the native ftp.exe client in Windows has a command that allows users to execute local operating system commands without direct access to cmd.exe. This usually comes in handy when there are a lot of restrictions around cmd.exe, and you don’t have change or write access to the file system. Below is a basic overview of how to use the FTP client to obtain a directory listing.
- Double-click ftp.exe, the console will launch
- Type “!dir” to get a directory listing
Below is a basic screen shot example.
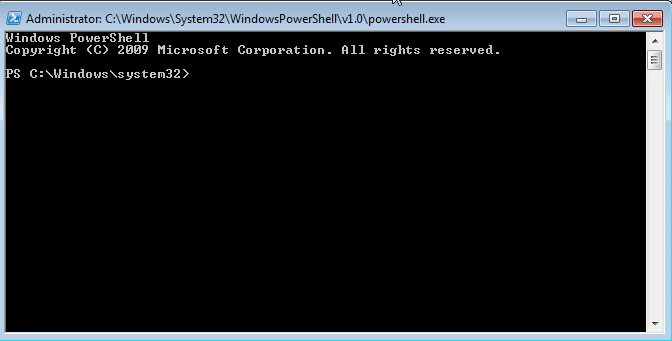
POWERSHELL.exe
PowerShell provides its own console with a bunch of cmd.exe aliases so that (for the most part) you can interact with it as though you were using cmd.exe. It also supports all the .net magic, which means you can basically run any command or call any API method that you have the privileges to. This is my preferred shell for that reason, but of course PowerShell must already be installed on the system. Below is a basic screen shot example.
Scripts of All Kinds
If script extensions such as .bat, .vbs, or .ps are configured to automatically execute their code via their intended interpreter, then in some cases it may be possible to drop a script that acts as an interactive console or downloads/launches your favorite Third-party applications.
Obtain Access to Native Management Consoles
It’s pretty well known that most kiosk systems are configured to run with local administrative privileges. So the native applications below should give you the means to access a full remote desktop or disable group policies that are making your life difficult. They can also come in handy when attacking Terminal Service and Citrix applications.
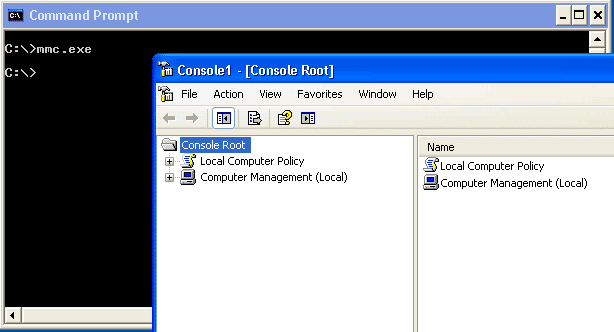
MMC.exe
MMC.exe allows users to build custom management control panels. It can be very handy for disabling restrictions on files, and other local configurations.
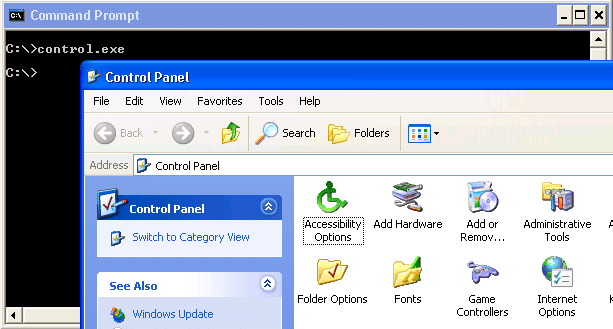
CONTROL.exe
Control.exe actually launches the control panel. Depending on the group policy this may or may not give you access to what you’re looking for.
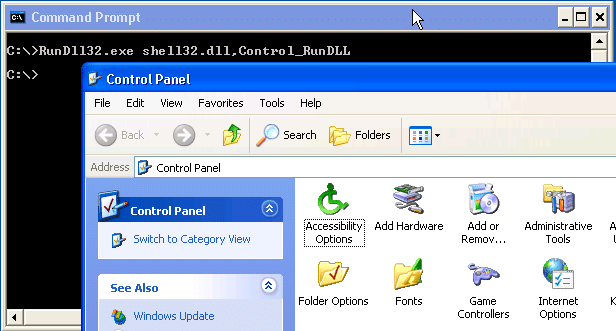
RUNDLL32.exe
Run dll can be used to execute dll functions from the command line. This includes the native API calls to launch management consoles. Below are a few examples that can be useful.
- Add/Remove Programs: RunDll32.exe shell32.dll,Control_RunDLL appwiz.cpl,,0Content Advisor
- Control Panel: RunDll32.exe shell32.dll,Control_RunDLL
- Device Manager: RunDll32.exe devmgr.dll DeviceManager_Execute
- Folder Options – General: RunDll32.exe shell32.dll,Options_RunDLL 0
- Folder Options – Search: RunDll32.exe shell32.dll,Options_RunDLL 2
- Forgotten Password Wizard: RunDll32.exe keymgr.dll,PRShowSaveWizardExW
- System Properties: Advanced: RunDll32.exe shell32.dll,Control_RunDLL sysdm.cpl,,4
- Taskbar Properties: RunDll32.exe shell32.dll,Options_RunDLL 1
- User Accounts: RunDll32.exe shell32.dll,Control_RunDLL nusrmgr.cpl
- Windows Firewall: RunDll32.exe shell32.dll,Control_RunDLL firewall.cpl
Below is an example screen shot.
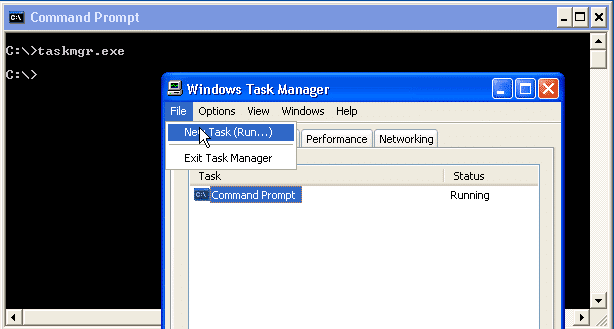
TASKMGR.exe
If you’re looking for something a little more intuitive than rundll32.exe, then taskmrg.exe may be for you. It will let you view all of the running process, logged in users, and provides functionality to run commands easily. Below is a basic screen shot.
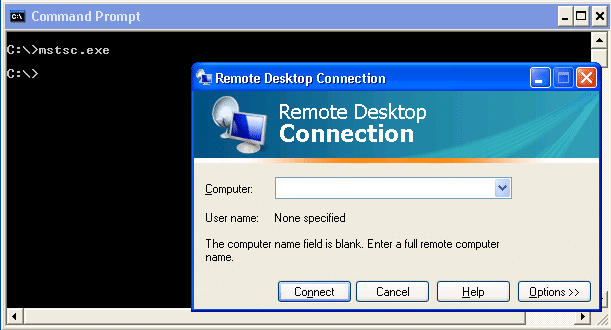
MSTSC.exe
Mstsc.exe is the remote desktop client for Windows. By remote desktoping to the Terminal Server or Citrix server that your already on, you may be able to obtain a full desktop without the original restrictions. It can make life easier if you’re trying to escalate privileges. Below is a basic screen shot.
Download Third Party Applications
In many cases leveraging native executables will be enough, but sometimes you may want to download your own tools to the target system. There are a ton of ways to accomplish this goal. However, I’m lazy so I’ve only included three common methods.
Terminal Services and Citrix clipboards
Based on my experience, Terminal Services and Citrix clipboards are left enabled to meet business requirement most of the time. That means that as an attacker you can simply copy and paste your tools to the remote server.
Web Server
Don’t forget that you can simply startup your own web server and download tools via the web browser. A lot of people like LAMP and WAMP for the sake of simplicity, but use what you like. Also, (as mentioned) iKat Desktop has some useful tools.
FTP Server
Similar to web servers, it’s easy to start up a malicious FTP server. As we have already seen, Windows has a FTP client installed by default that can be used to pull down tools to the target system. Also, don’t forget that Internet Explorer can be used as a FTP client with the “ftp://” protocol handler.
Useful Third Party Applications
There are a number of third party tools that can come in handy when breaking out of applications. If policies and privileges are very restrictive it may be easier to simply upload your own application to do simple things like manage the registry, navigate the file system, and obtain an interactive console. So below I’ve provide a few tools that I’ve had success with. Also, iKat has a lot of fun options.
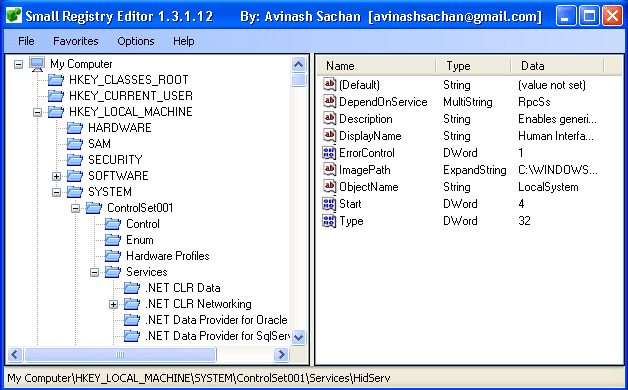
Alternative Registry Editors
Oh registry how I love thee. If you’re looking for a few registry editors that won’t be blocked by the standard group policy then look no further. Simpleregedit and Uberregedit are GUI tools that can be used to edit Windows registry. Below is a basic screen shot.
They can be downloaded from the links below.
- https://sourceforge.net/projects/simpregedit/?source=recommended
- https://sourceforge.net/projects/uberregedit/
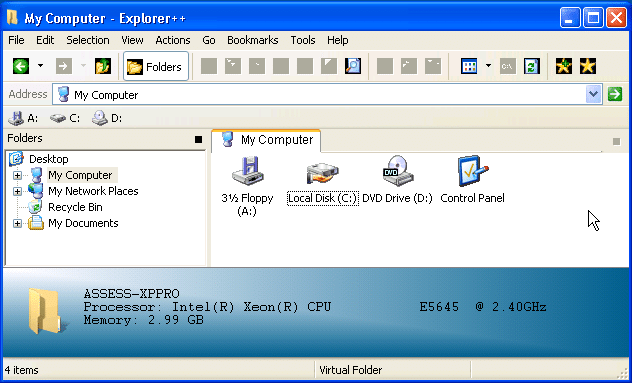
Alternative File System Editor
I like this little single executable file explorer. It’s fast and easy to use. Best of all it will bypass all of the folder restrictions applied by group policy. Below is a basic screen shot.
Explorer++.exe can be downloaded from the link below. However, be aware that there are separate executables for x64 and x86 architectures.
Alternative Interactive Console
Console.exe may sound generic, but it gets the job done when harsh group policy restrictions are in place. It does consist of four files, but does not need to be “installed” so it’s still very portable. Below is a basic screen shot.
Console.exe can be downloaded from the link below.
Wrap Up
This blog has provided some insight into common break out methods that can be used for Terminal Services, Citrix, and kiosk applications. As with any game – your offense is usually better when you have a solid understanding of the your opponent’s defensive strategy. So I highly recommend looking at the hardening guides provided below by Microsoft and Citrix to get an understanding of what administrators are/should be doing. Hopefully using the blog and guides together will help you identify common security weakness before the bad guys do. Good luck and hack responsibly.
References and Links
- https://www.virtualizationadmin.com/articles-tutorials/terminal-services/security/locking-down-windows-terminal-services.html
- https://technet.microsoft.com/en-us/library/cc264467.aspx
- https://technet.microsoft.com/en-us/library/cc758409(v=ws.10).aspx
- https://msdn.microsoft.com/en-us/library/aa767740(v=VS.85).aspx
- https://msdn.microsoft.com/en-us/library/aa767731(v=VS.85).aspx
- https://msdn.microsoft.com/en-us/library/cc848897(v=vs.85).aspx
- https://ha.cked.net/Windows/index.html
Explore more blog posts

Navigating Cybersecurity Regulations Across Financial Services
Learn about five areas businesses should consider to help navigate cybersecurity regulations, such as the Digital Operations Resiliency Act (DORA).

A New Era of Proactive Security Begins: The Evolution of NetSPI
Introducing The NetSPI Platform, the proactive security solution used to discover, prioritize, and remediate the most important security vulnerabilities. Plus, get a first look at NetSPI’s updated brand!

Penetration Testing: What is it?
Learn about 15 types of penetration testing, how pentesting is done, and how to choose a penetration testing company.